Lakehouse fine-grained access control
Demo Video

Client Tool
This demo will use a browser to access the AWS Management Console and Amazon Redshift Query Editor from the AWS console.
Before you Begin
Ensure you have access to the AWS Console and an existing Redshift cluster with permissions to modify it. Capture the following parameters from the launched CloudFormation template as you will use them in the demo.
https://console.aws.amazon.com/cloudformation/home?region=us-east-1#/stacks?filteringText=&filteringStatus=active&viewNested=true&hideStacks=false
- RedshiftClusterEndpoint
- RedshiftClusterPort
- RedshiftClusterUser
- RedshiftClusterPassword
- RedshiftClusterDatabase
- RedshiftClusterRoleArn
- RedshiftClusterRoleLFAccessControlArn
- GlueExternalDatabaseName
Some Isengard accounts may have an IAM Principal already setup as Database Creators. You may have to do this step to clear that IAM Principal, see steps below.
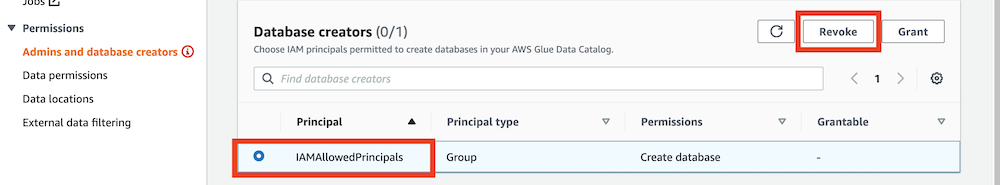
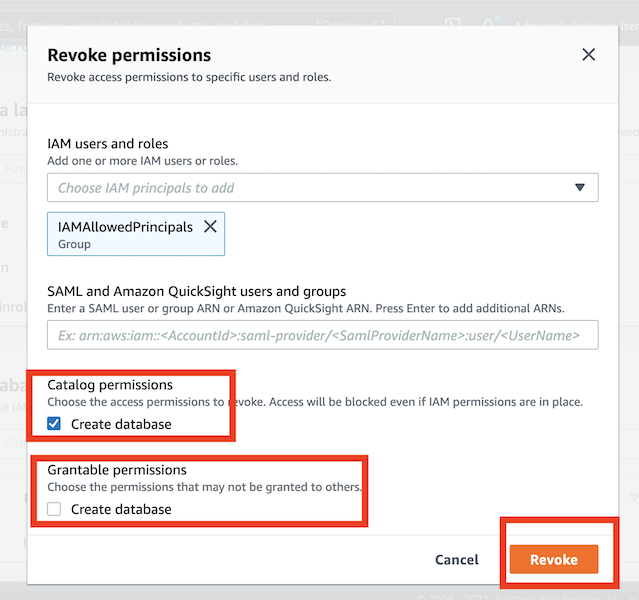
- Navigate to the AWS Lake Formation on AWS console and select
Admins and database creatorsfrom the left menu - If you see an entry under the
Database creatorssection, please select and revoke it by clicking theRevokebutton. See screenshots below. - If the IAM Principal role also has access at the table level, you may also need to revoke that in order for the revoke access steps to work as designed.
Challenge
Rachel has been tasked to setup column-level access control on data stored in Amazon S3 using AWS Lake Formation.Amazon Redshift’s integration with AWS Lake Formation allows to implement fine-grained access control on the managed data lake while still being able to query the data lake with Amazon Redshift Spectrum. She will work with Miguel to accomplish some of the tasks. To accomplish this task she will perform the following tasks:
- Verify access to external table
- Revoke access to external table
- Grant and verify column level access on the external table
Verify access to external table
| Say | Do | Show |
|---|---|---|
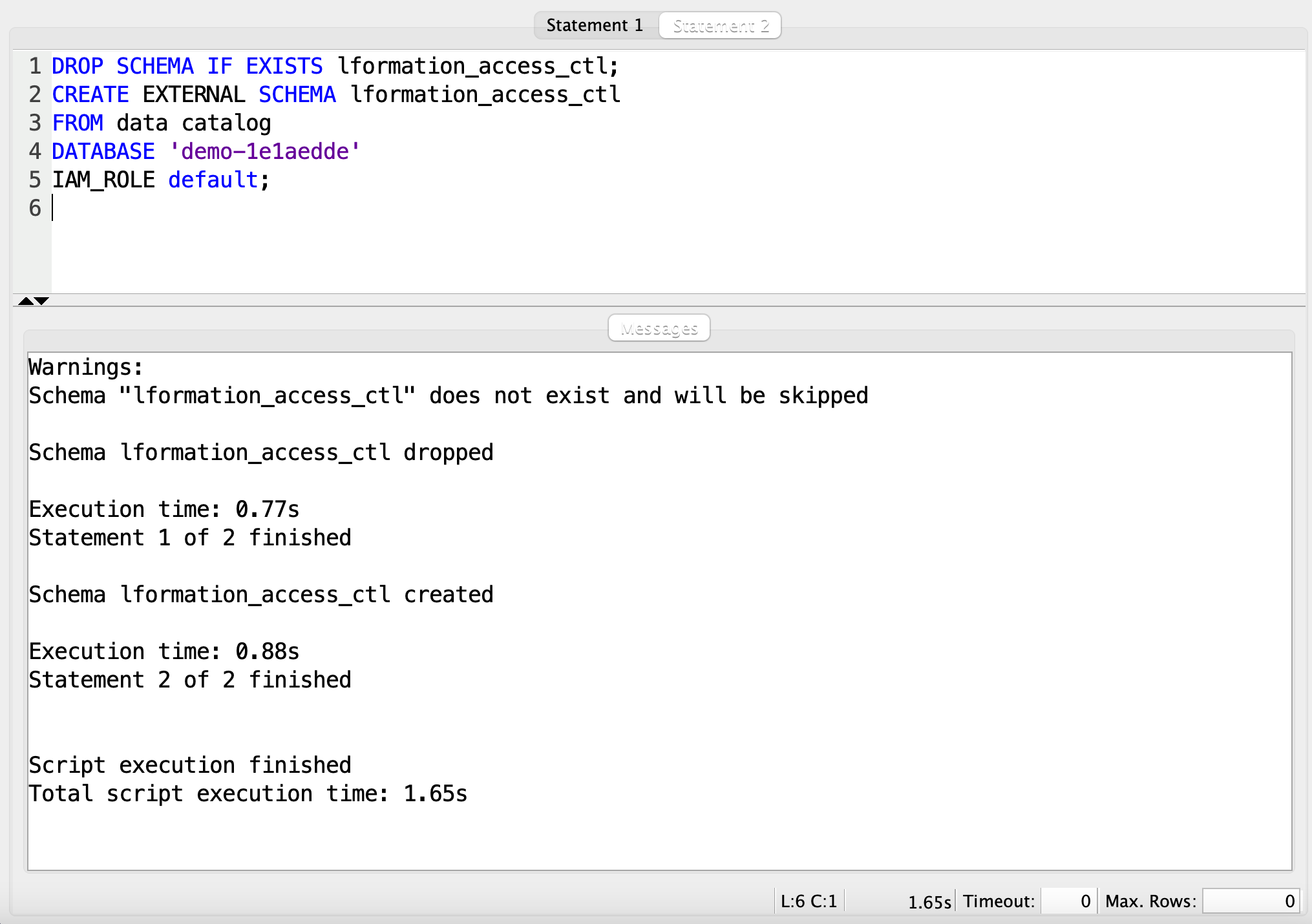
| Miguel needs to create an external schema in Redshift which references a table in the external Data Catalog and authorizes your cluster to access Amazon S3 |
Execute the following SQL statements, replacing with output values captured from Cloud Formation. This will create an external schema and the IAM role grants access to the underlying data.
|
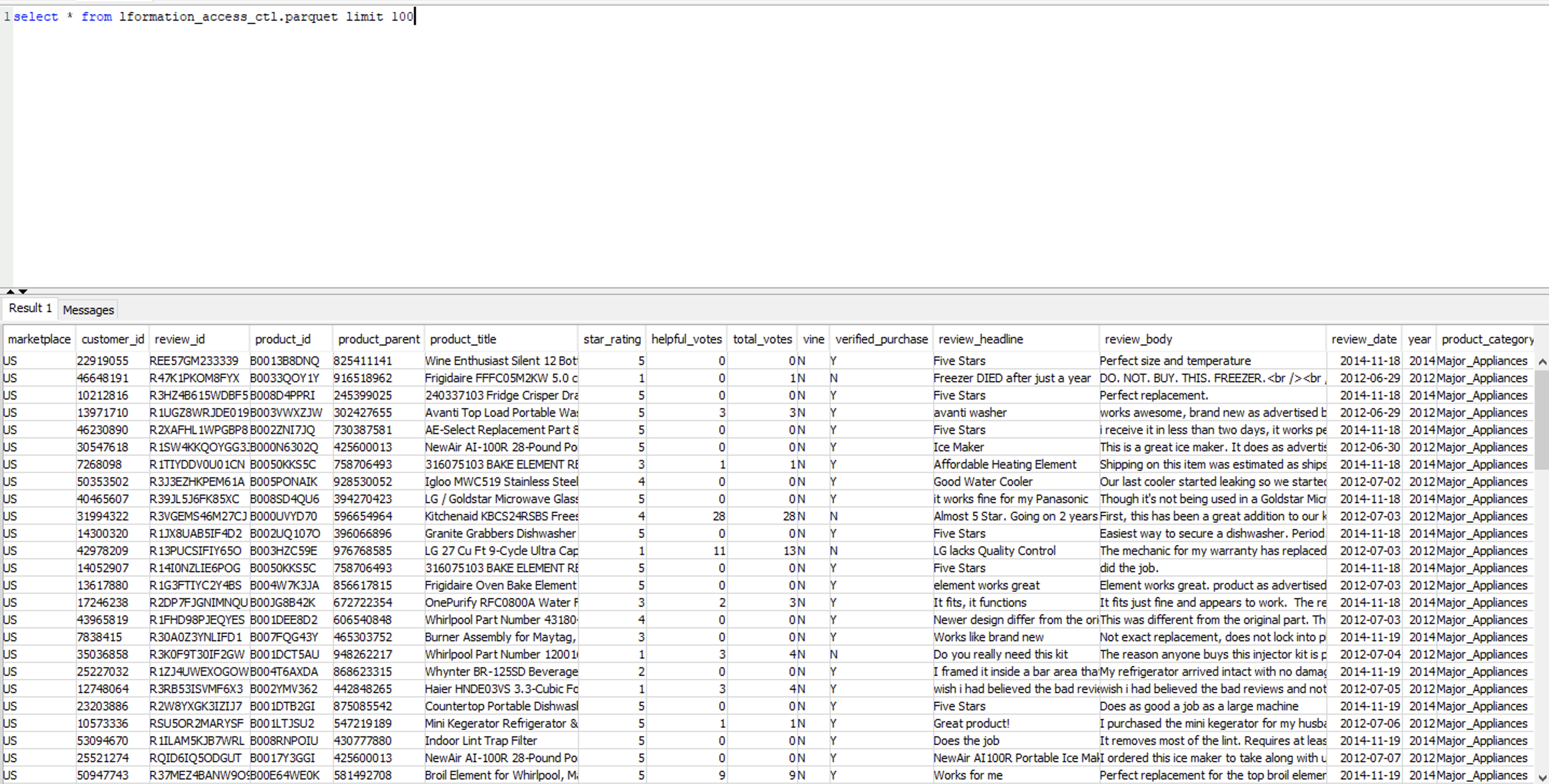
| Miguel needs to verify that he can execute queries and see all the data in the table. |
Execute the following SQL statement in Redshift Query editor or a SQL Client.
|
|
Revoke access to external table
| Say | Do | Show |
|---|---|---|
| Rachel will use AWS Lake Formation from the AWS Management Console to revoke the current access from the IAM role. |
Follow the steps below to revoke access:
|
|
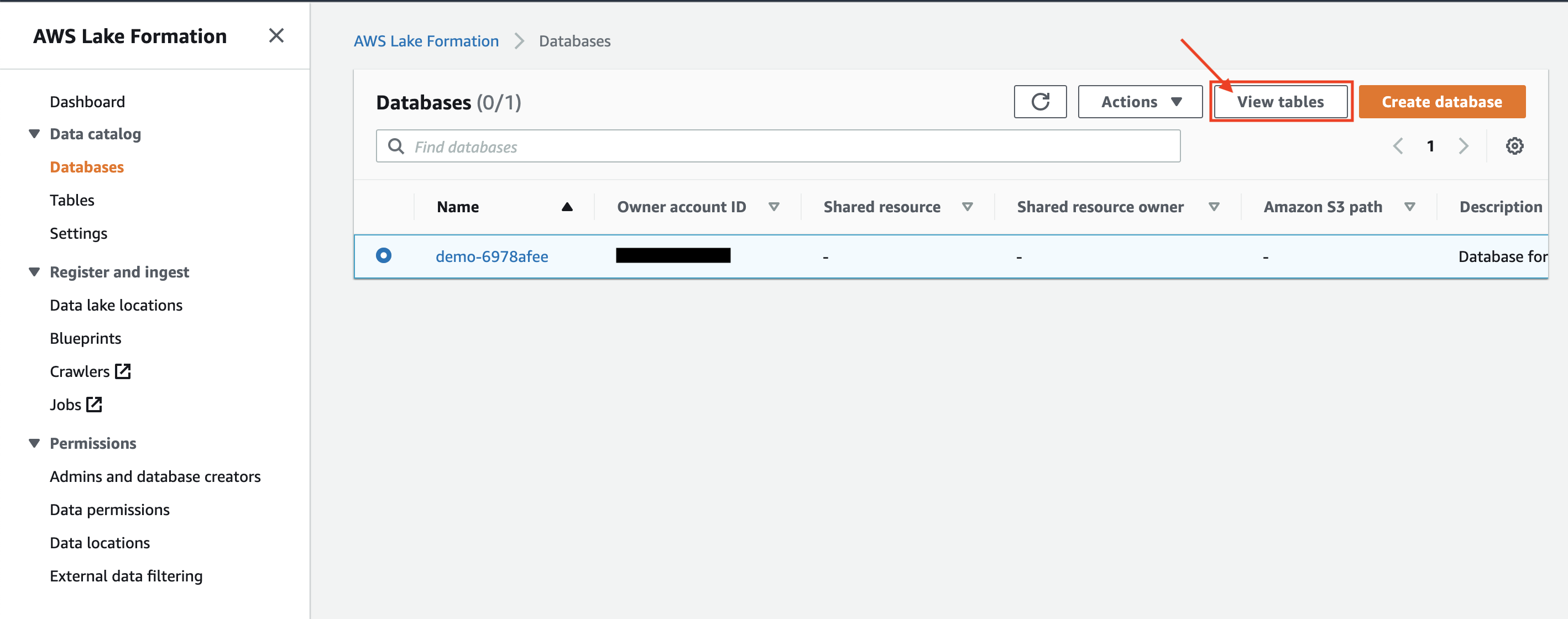
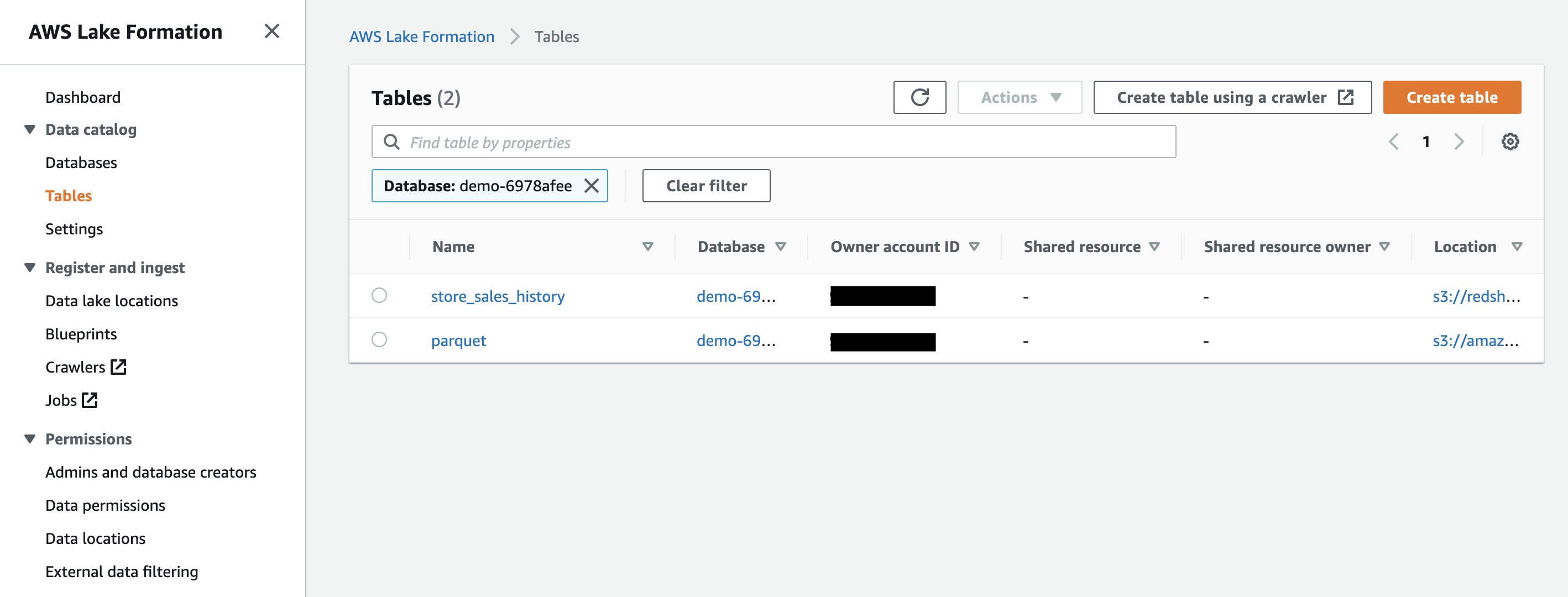
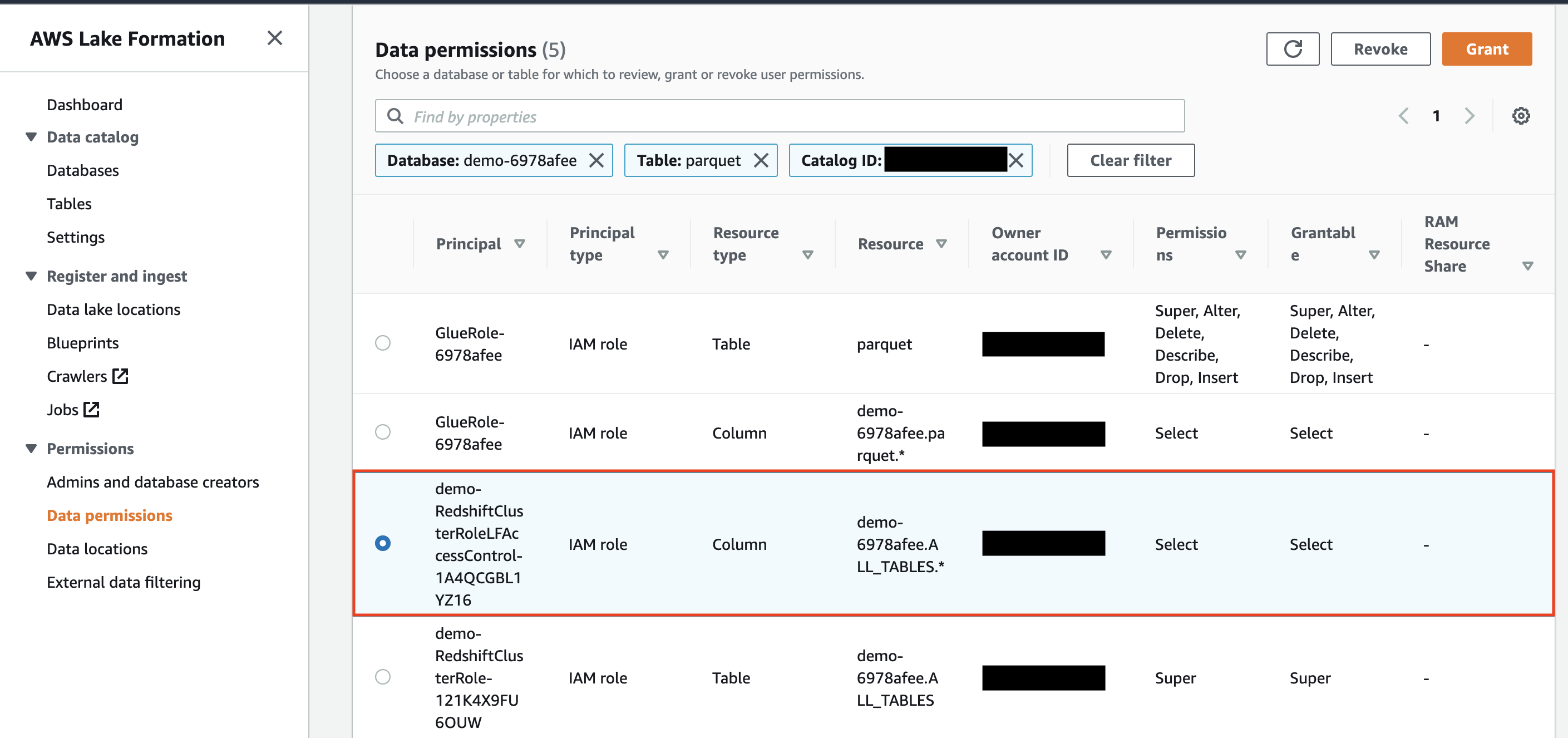
| Rachel will see the list of the tables in the database and selects the table to revoke access. |
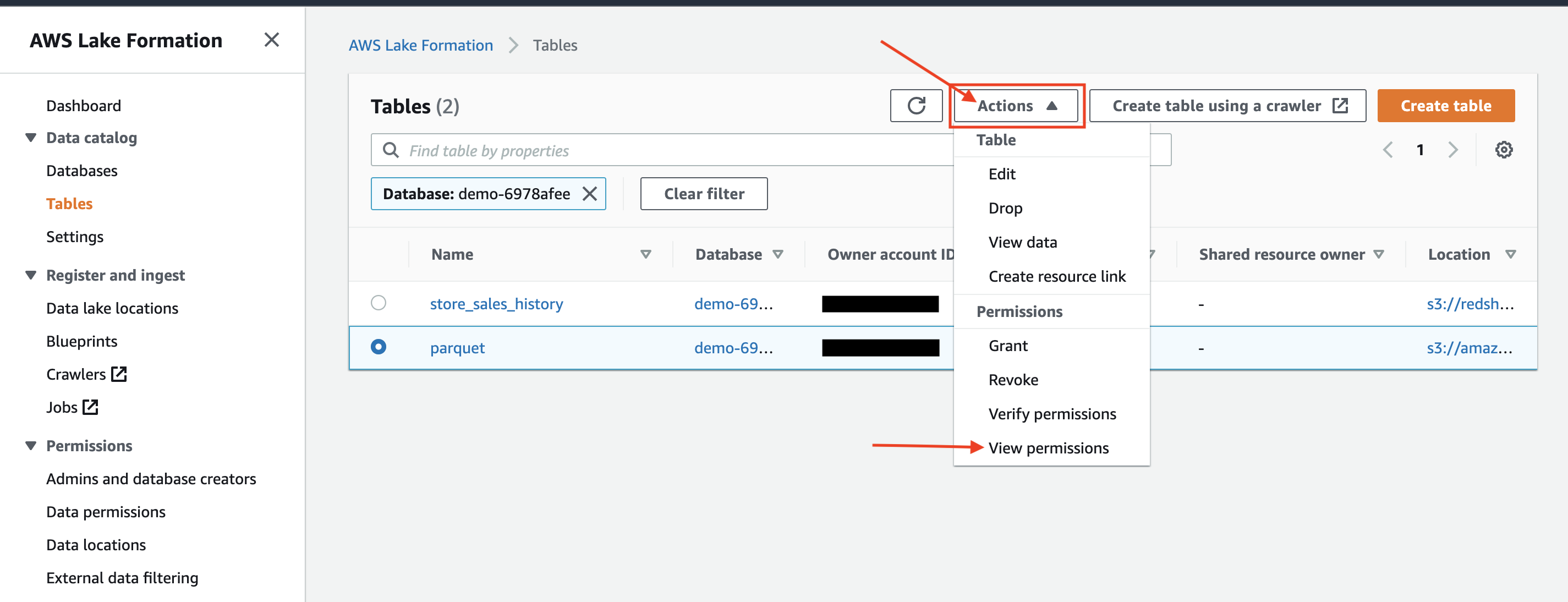
Choose the parquet table and click on Actions-> View Permissions. Notice the current permission of IAM role .
|
|
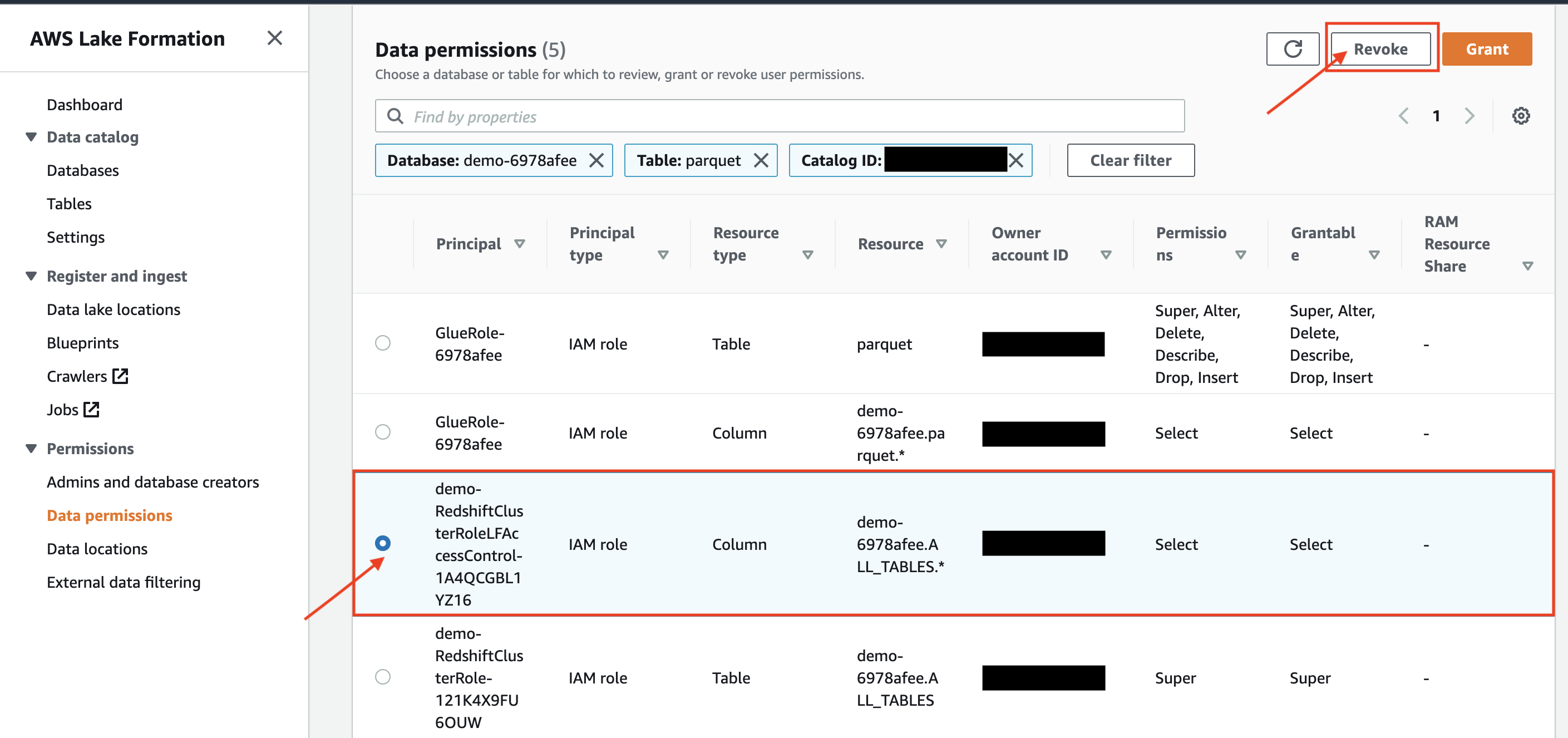
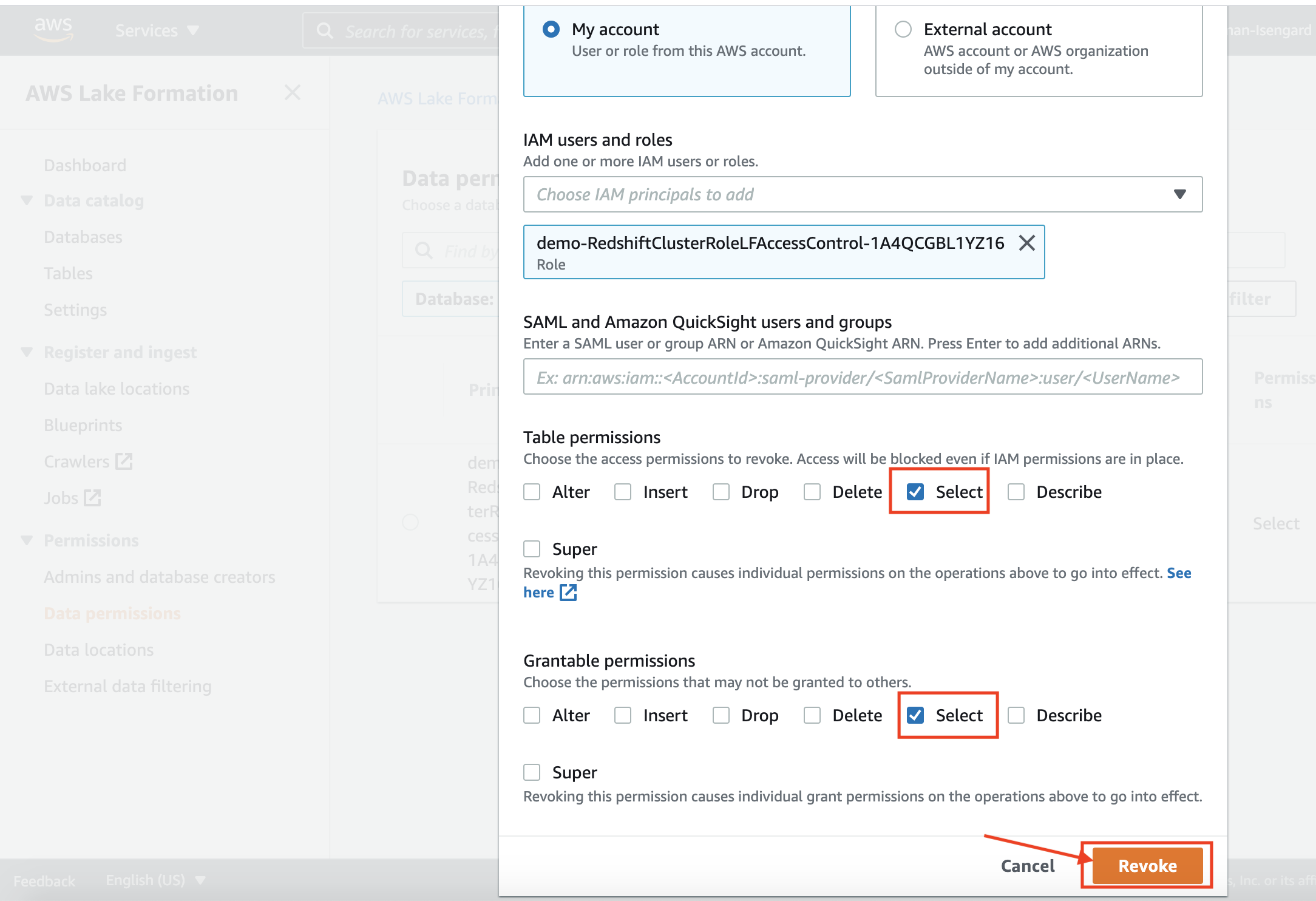
| Rachel will now revoke the permissions of IAM Role on the external table. |
|
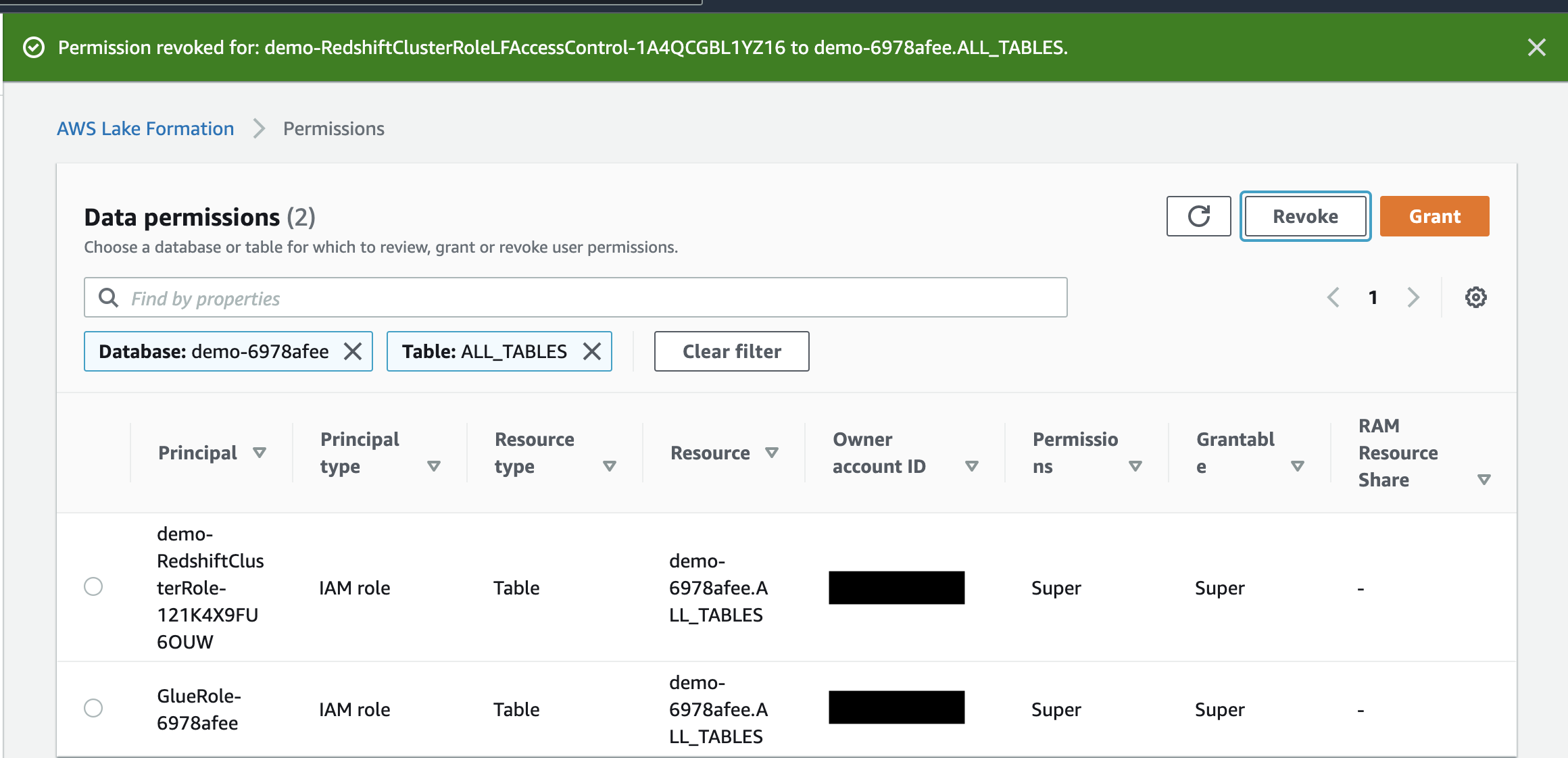
| Miguel will verify that the IAM role is denied access on external table |
Execute the following SQL statement and confirm access denied.
|
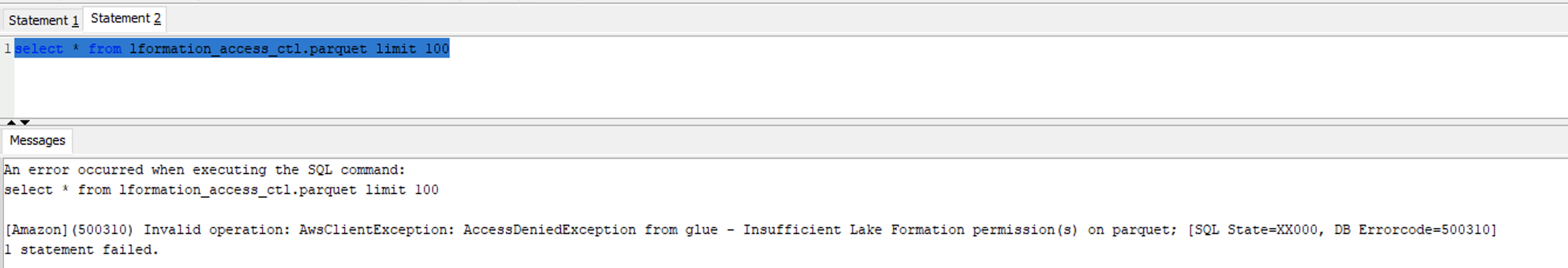
|
Grant and verify column level access on the external table
| Say | Do | Show |
|---|---|---|
| Rachel will grant access to the IAM role on specific columns of the external table. She is doing this because this role has restricted access to these data columns. |
In the Data Permissions section of Lake Formation AWS Console, click on the Grant button:
|
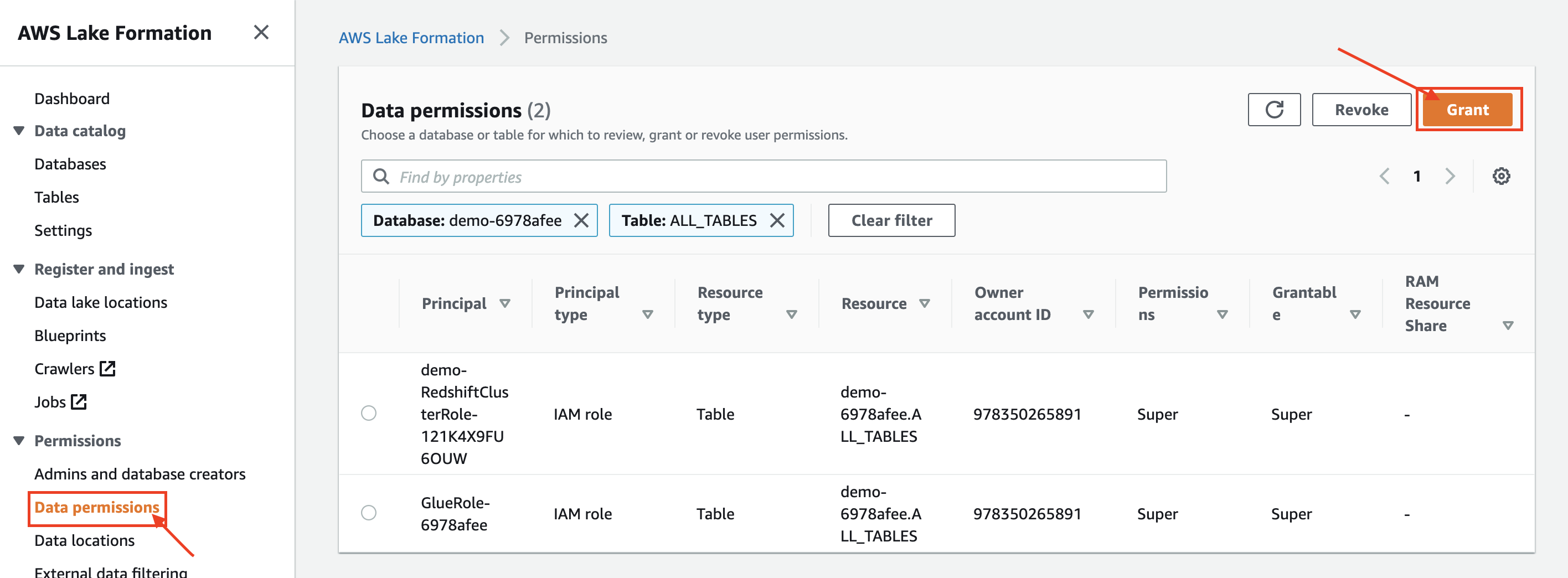
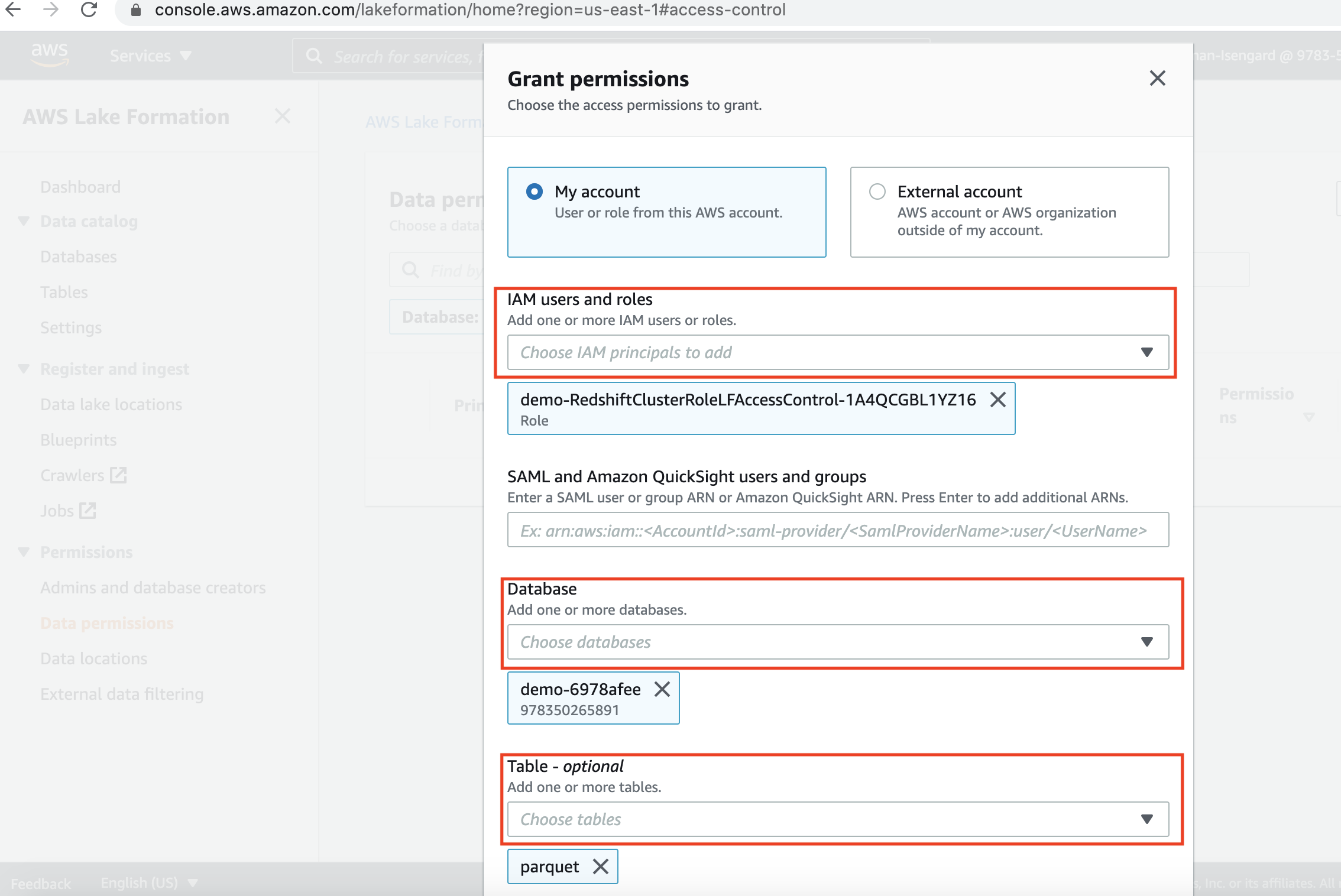
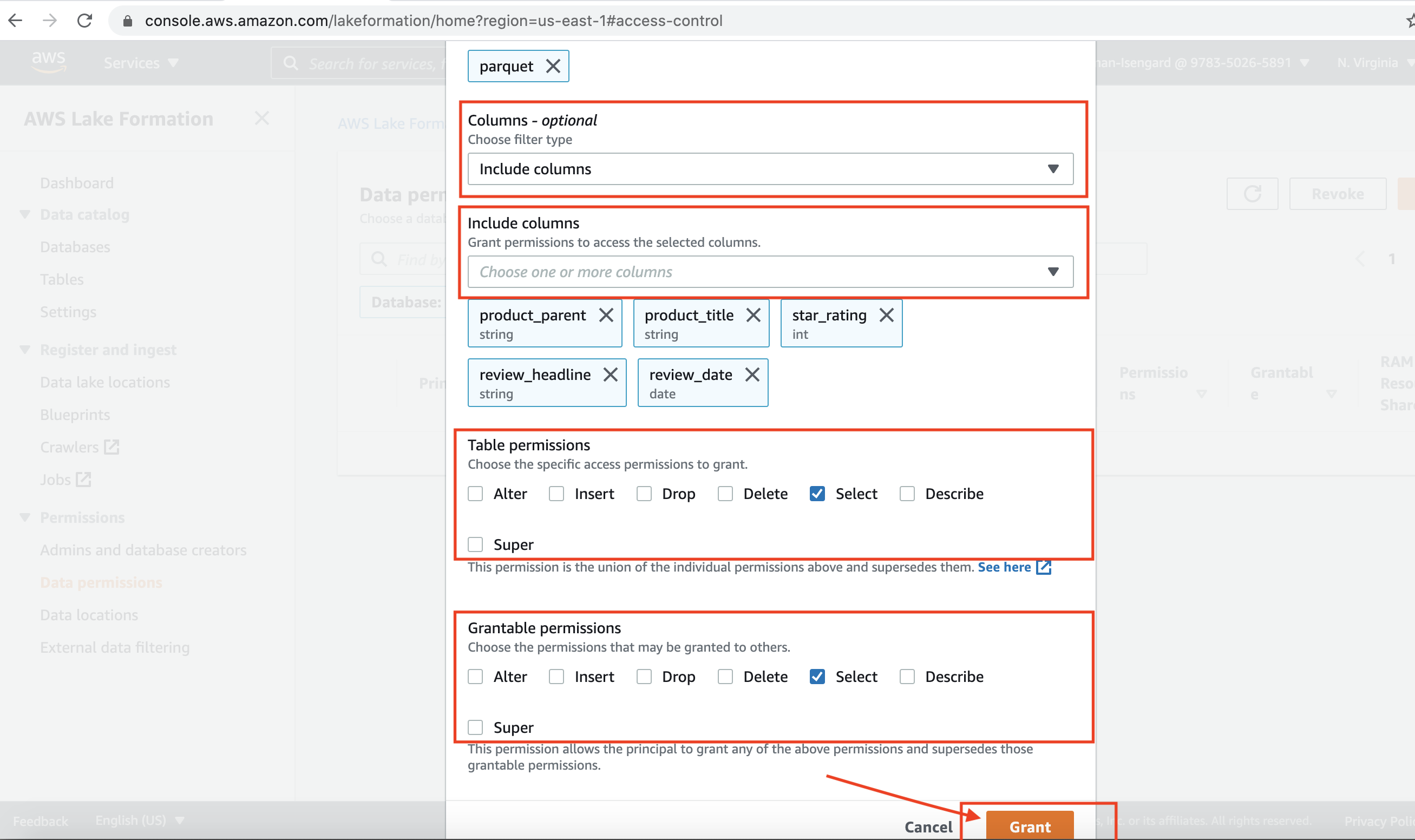
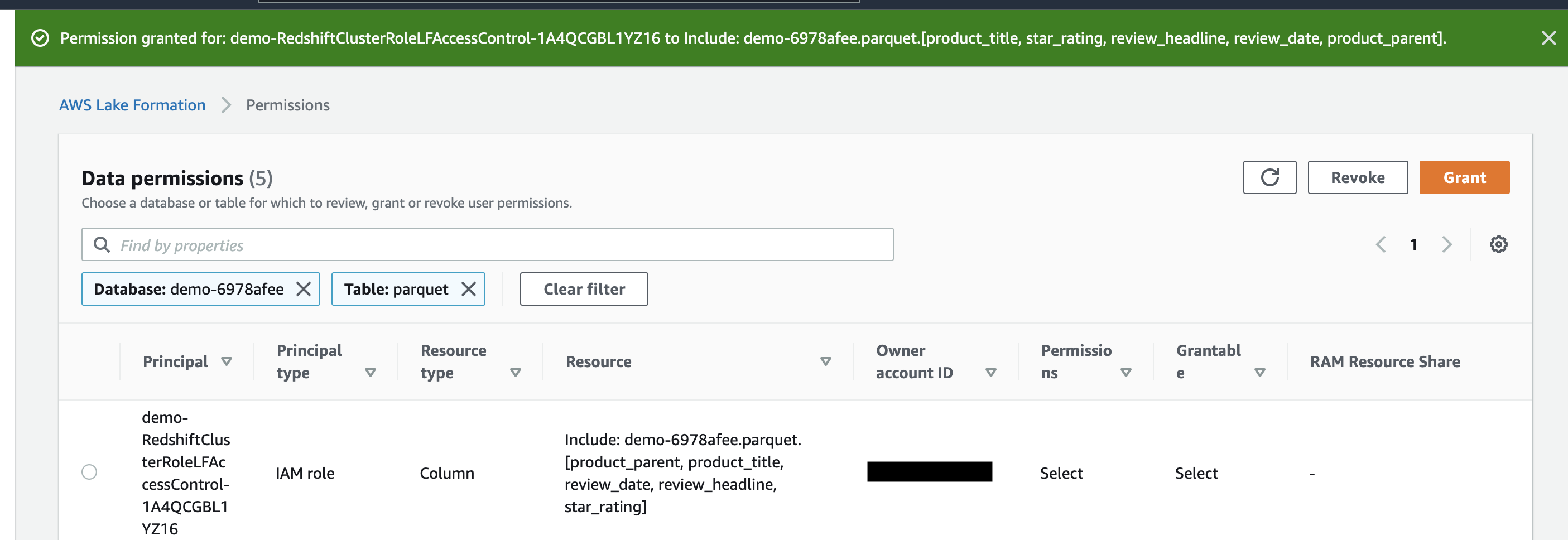
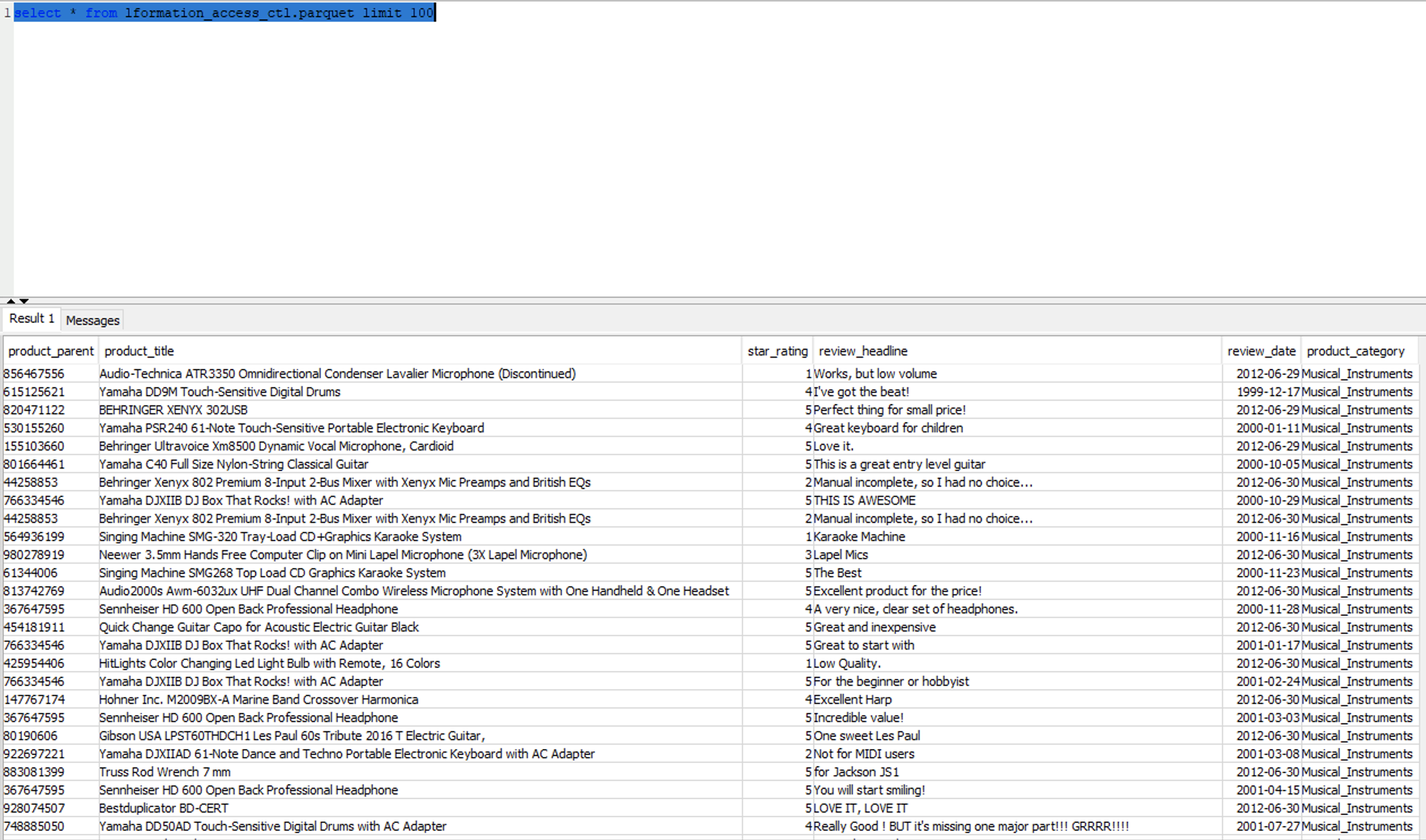
| Miguel will verify access on external table with the columns where access was revoked no longer accessible. |
Execute the following SQL statement. In the query result only the columns having access to the IAM role is visible.
|
|
Before you Leave
To reset your demo for a re-run at a future point in time. Grant permissions to the role in Lake Formation and run the following query in Redshift:
DROP SCHEMA lformation_access_ctl;
If you are done using your cluster, please think about deleting the CFN stack or to avoid having to pay for unused resources do these tasks:
- pause your Redshift Cluster
- pause the dms tasks